- Why good security practices matter for remote workers
- Invest in a virtual private network (VPN)
- Enable two-factor authentication (2FA)
- Avoid unsafe network connections
- Be wary of social media
- Create strong passwords
- Keep software updated
- Regularly back up data
- Conduct regular virus scans
- Be careful what you install
- Watch out for phishing scams
- Protect your device from theft
- Conclusion
In many ways, remote working is the future. Remote work opens up a world of endless possibilities for flexible work, especially for people often excluded in the traditional workplace. However, it does open remote workers to risks that must be managed to protect yourself and your company's data.
According to Gallup's 2017 State of the American Workplace report, 43% of American employees tried working remotely in 2016. Up from 39% in 2012, experts expect the remote working trend to continue, with more than half of all employees having a remote job by 2025.
There are several reasons why companies are starting to focus more on hiring remote workers. With remote working, employees can save time, effort, and costs from traveling to and from the office. In addition, remote working makes working more accessible for those who typically struggle to work in traditional office environments, such as people with disabilities and single parents.
However, while there are many benefits to working remotely, there are also security risks that employees should know and manage. Here's why it matters.
Why good security practices matter for remote workers
In 2017, Symantec reported that nearly a quarter of organizations had experienced increased attacks targeting remote workers. One of the reasons for this is that remote workers often use their own devices, which may not be as secure as devices issued specifically by companies. Additionally, they may not have the same level of access to security resources as on-site employees.
According to the 2019 Cost of a Data Breach Report from Ponemon Institute, the average total cost of data breaches is $3.9 million. With this, it’s no wonder that companies are starting to realize how preventing security issues is always better than dealing with its poor aftermath, especially those which have embraced remote work. This article will discuss the best remote work security practices to protect your and your company's data.
Invest in a virtual private network (VPN)
One of the essential security practices for remote workers is to use a virtual private network (VPN), a secure connection that encrypts data and routes it through a secure server.
Although VPN can't completely prevent hackers from accessing your device, it can help discourage anyone from intercepting your data. While some employers provide their employees with a VPN service, many free and paid options are also available.

To learn even more about managing remote teams and keeping employees working at home highly engaged, download our ebook now.
Download nowEnable two-factor authentication (2FA)
Another important security practice is to use two-factor authentication (also known as two-step verification). 2FA is an extra layer of security that requires you to enter a code in addition to your password when logging into accounts.
With 2FA, codes are sent to your phone or email or generated by an app such as Google Authenticator. With two-factor authentication, you can protect your accounts even if your password is compromised.
Avoid unsafe network connections
Employees working remotely should also be aware of public Wi-Fi risks, often unsecured and unprotected. However, hackers can also still intercept your data using supposedly safe and password-protected Wi-Fi, such as hotels or cafés.
If possible, it's preferable to bring your Wi-Fi stick or use your phone mobile hotspot instead of networks owned by other people. With this, you significantly reduce your risk of hackers infiltrating your device.
Be wary of social media
While everyone seems to be on social media, it's important to remind employees that anything you post on social media is public information. Generally, it's best to be mindful of webcam protection and be careful about posting sensitive information that could reveal company documents, private meeting rooms, etc.
Aside from this, it's best to avoid posting your precise location, especially when you're on holiday, which can inform thieves that you're not at home. With this, they are more likely to target your house for theft.
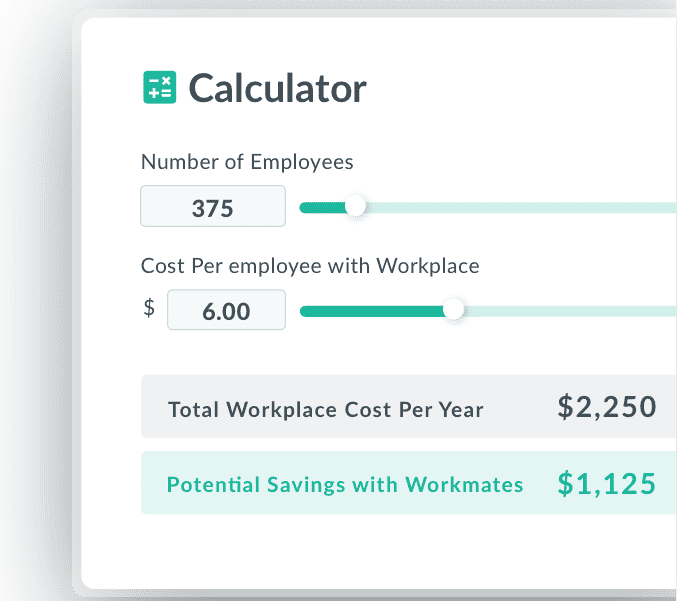
Find Out How Much You Can Save by Switching to Workmates.
and save upwards of 60%
Create strong passwords
Hackers commonly gain access to accounts is by guessing or brute-forcing passwords. To avoid the risks of weak passwords, here are some tips on how to create strong passwords:
-
Use passwords at least eight characters long.
-
Combine uppercase and lowercase letters.
-
Add numbers and special characters.
-
Don’t use obvious passwords, like your name, birthday, or pet’s name.
-
Avoid using the same password for multiple accounts.
Alternatively, you can invest in password managers to quickly generate and keep strong passwords for all your online accounts. Lastly, it's best to never share your passwords, even with those you love.
The 40 Best Thank You
Messages for Colleagues
building a positive and engaged culture at your company.

Keep software updated
Among the variety of ways hackers typically gain systems access, outdated operating systems is one of the most common. In numerous instances, hackers can exploit vulnerabilities in devices to access your device, which may include company information.
Aside from investing in antivirus protection, updating your software can help protect yourself and your company from known vulnerabilities. Thankfully, many software programs have automatic update features that can help make this process easier.
Regularly back up data
While it's crucial to purge files from your device regularly, it's also essential to ensure you don't lose the important ones. By removing your personal information from the internet and backing up your data, you can protect yourself even if your device is lost or stolen. In addition, if you ever become a victim of ransomware, backup data helps make sure your company isn’t inconvenienced during the investigation.
In general, there are two main ways to backup data: hardware and software. For example, you can use a USB, external hard drive, or cloud storage service for your important files and documents.
Although there are many options to backup your data, the most effective one will always be the method you can commit to regularly doing. With this, it's best to choose a backup plan that is right for you and your lifestyle.
Conduct regular virus scans
Since remote teams often use their own personal devices, it's important to remind them to scan their machines for viruses regularly. While it’s not always possible to monitor your device 24 hours a day, there are plenty of apps which have breach notification features.
Viruses can sometimes slip through the cracks, primarily if you work in public areas and use Wi-Fi in hotels or coffee shops. If possible, it's best to invest in apps that you can use to scan your device on-demand or do it automatically.
Be careful what you install
When working remotely, you must be careful about the applications and programs you install on your devices. Hackers often develop apps that look similar to legitimate apps to avoid. Here are some ways to avoid downloading questionable apps on your device:
-
Download apps from the App Store, Google Play, or other trusted platforms.
-
Avoid purchasing activation codes from third-party sellers.
-
Read the app permissions carefully.
These ads, apps tend to ask for access to your contacts, location, and other personal information, even if they're not necessary for the features you need. Aside from being careful what you install, it's best to only grant permission to apps you trust that need the information.
Introduction to Conflict in the Workplace
(and How it Erodes Productivity & Culture)
Watch out for phishing scams
These days, companies should also train employees on how to spot phishing emails. Phishing is a type of online scam where criminals send emails that appear to be from a legitimate source. However, these emails are used to trick people into giving them personal information or money.
While these emails can look very convincing, there are usually some red flags that you can identify. Here are some of them:
-
Typos or grammatical errors
-
Words with wrong spelling
-
Suspicious attachments or links
If you receive a suspicious looking email, do not open it or click on any links. Instead, report it to your IT department for threat management. Afterward, you can proceed to delete the email and block the user.
Protect your device from theft
Because remote working lets you work from home or anywhere with a stable internet connection, many remote workers tend to go to places like coffee shops or co-working spaces. However, these places can also invite enterprising thieves looking to make a quick buck.
Even when you're not using your devices in a public place, it's essential to keep them with you. Avoid leaving your laptop, mobile phone, or tablet when you use the restroom or buy a drink. If you must go and leave your device in a public place, lock it up, hide it from view, or ask a friend to watch it for you.

HR mistakes impact your entire organization. Learn how to avoid the 12 most common mistakes with our free ebook.
Download nowConclusion
When it comes to staying safe while working remotely, it is best to approach internet security holistically, all days a week. Aside from increasing remote work productivity, it's also essential to know how you can keep yourself safe from hackers and other bad actors.
Although no method can guarantee to prevent all security threats, taking multiple precautions can significantly reduce your risk of becoming a cyberattack victim. Using Workmates by HR Cloud, you can help engage your employees with regular tips on how to protect themselves while they're working remotely.
About Author:
This article is written by a marketing team member at HR Cloud. HR Cloud is a leading provider of proven HR solutions, including recruiting, onboarding, employee communications & engagement, and rewards & recognition. Our user-friendly software increases employee productivity, delivers time and cost savings, and minimizes compliance risk.
Stop Conflict Before it Begins with
a Culture of “Thank You”
Keep Reading
Upskilling and Reskilling: Preparing the Workforce for a Tariff-Impacted Economy
Recent shifts in global trade policies have led to a new wave of tariffs impacting
Retention Reset: How to Keep Your Best Talent in 2025
More employees are walking away from their jobs in 2025 not just for better pay, but for