
 Cut onboarding time
by 60%—here's the
Ultimate Checklist
that helped do it.
Cut onboarding time
by 60%—here's the
Ultimate Checklist
that helped do it.
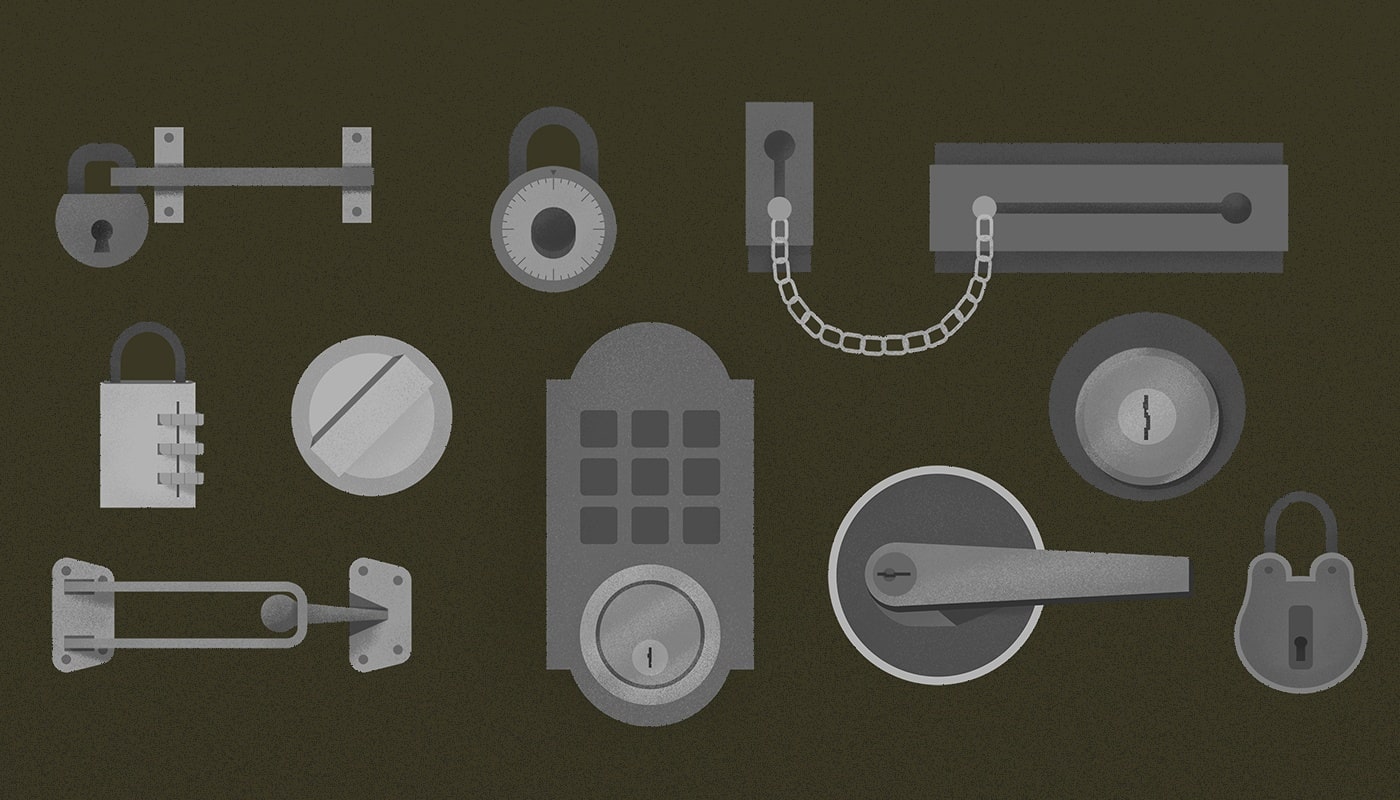
Digital data security is a hot topic. With so many potential threats to your private information, ensuring the security of your company's important details is essential.
But rather than just tell you that HR Cloud is "secure" and that all your digital data stored in our system is safe, we want to take a moment to tell you both why and how.
After reading this post, you'll have a firm understanding of the process we've developed to shield your data from prying eyes and exactly why we take these security measures.
The HR Cloud Approach to Data Security
HR Cloud uses a multi-faceted architecture designed to protect and secure customer data. What does that mean? It means your data is completely safe inside our system!
Our team has worked (and continues to work) extremely hard to construct a digital environment that is highly resistant to hacking attempts by:
Social Intranet Software that Encourages Employee Communication
-
Ensuring your data is securely transmitted over the internet.
-
Ensuring your data is protected from physical tampering.
-
Partitioning the environment.
-
Using data filtering products from multiple vendors.
-
Protecting your information from both known and unknown attacks.
-
Quickly installing patches.
-
Using the same tools hackers use.
-
Training our personnel on proper handling and access.
Let’s examine each of these in more detail and discover why they're important to you and your business:
Ensuring Your Data is Securely Transmitted Over the Internet
Every browser supports secure transfers of data by referencing a “padlock” in the address URL bar. Secure transfers of data mean using https instead of http. Https has evolved over the past few years as older data transfer algorithms have been broken. In the industry, this is called “secured data-in-transit”.
HR Cloud currently uses a protocol called TLS/1.2 which is the latest, strongest, unbroken method to securely transfer your data.
Ensuring Your Data is Protected From Physical Tampering
Data can potentially become compromised when a faulty drive used to store customer information is removed and replaced with a fresh one. If the faulty drive is partially readable, customer data may be exposed to unknown sources.
To solve this problem, HR Cloud currently uses Dell/EMC hardware and AES256 bit encryption to encrypt all data and backups. This is known as “secured data-at-rest”.
Partitioning the Environment
Think of Fort Knox — before you can see the gold bars, you're required to pass through multiple secure doors. That way, if one of the doors has a weakness, the other doors will still protect the gold inside.
Likewise, HR Cloud uses multiple doors (zones) to protect your data. If one (or more) zones are compromised, your information is still protected.
Using Data Filtering Products From Multiple Vendors
Data filtering products, typically called firewalls, are used to investigate and only allow authentic customer traffic between zones. Using firewalls from multiple vendors protects customer data if a vulnerability in a vendor is discovered.
HR Cloud uses next generation filtering products to protect your information against unauthorized applications and data transfers.
Protecting Your Data From Both Known and Unknown Attacks
There are two types of attacks: ones that you're aware of and ones that you're not. These types of attacks can be profiled and scanned for unusual or malicious behavior. But sometimes attacks can come before a software has been patched by the vendor. These are called “zero day attacks”.
HR Cloud uses next generation endpoint and network protection to identify and protect your data from these types of attacks.
Quickly Installing Patches
Many customer data breaches occur because companies do not patch their software in a timely fashion. The consensus best practice is to apply security patches immediately and any other patches within a few weeks.
HR Cloud follows this best practice.
Using the Same Tools Hackers Use
Many companies deploy tools to try to “hack" themselves. This can quickly identify if there are any vulnerabilities in the systems used to store and process customer data. These tools can also be used to verify other defensive mechanisms.
HR Cloud routinely scans itself and quickly acts to resolve all relevant vulnerabilities.
Training Our Personnel on Handling and Access
Many exploits happen not because of someone hacking the servers, but through a company’s employees. This type of exploit is called "social engineering".
HR Cloud routinely conducts exercises where our employees are trained to detect and report various forms of social engineering.
It's also important to note that secure access to customer data requires more than the use of a strong password. Instead, it's important to use a strong password and another device as a prerequisite to access customer data.
This is called "multi-factor authentication": you input something you know (a password) and something that changes frequently (a device with numbers) before you are allowed to access data.
HR Cloud uses multi-factor authentication for all administrative access.
Your Data is Secure Inside the HR Cloud System
As you can see, we take data security very seriously at HR Cloud. When your information is stored in our system, you can rest easy knowing that it's protected by our numerous security measures!
If you have any questions regarding data security and the ways HR Cloud handles potential threats, please contact us. Our team is more than happy to further explain our many security measures and make sure you feel comfortable using our system.
HR Cloud is a leading developer of HR software & HRMS solutions for small and medium size businesses that have high turnover. HR Cloud's Onboard is market leading technology for effective new hire onboarding and Workmates enables employee engagement simply and easily. Founded in 2012, our HRIS empowers teams to easily onboard new hires, manage employee data, create a company social network and support employee development.

Keep Reading
AI for Frontline HR: Moving Beyond Sentiment Analysis to Build Tomorrow's Workforce Management Engine
TL;DR: While most organizations limit artificial intelligence in human resources to basic
Best HR Tools for Compliance Automation (and Why HR Cloud Leads the Pack)
The Compliance Catch-Up: What HR Needs to Fix Before Mid-Year Audits
By May, most HR teams have settled into the rhythm of the year. But compliance? That
Like What You Hear?
We'd love to chat with you more about how HR Cloud® can support your business's HR needs. Book Your Free Demo

Build a Culture of Recognition. Boost Engagement. Guaranteed.
Workmates empowers employees to stay informed, connected, and appreciated—whether they’re on the front line, in the office, or remote. Recognition drives 12x higher engagement.Trusted by industry leaders in every sector




Cut Onboarding Costs by 60%.
Take the confusion and follow-ups out of onboarding with automated workflows, digital forms, and structured portals—so new hires ramp faster 3X quicker.Trusted by industry leaders in every sector