Redefining Cybersecurity Goals: The Evolving Role of The HR Department


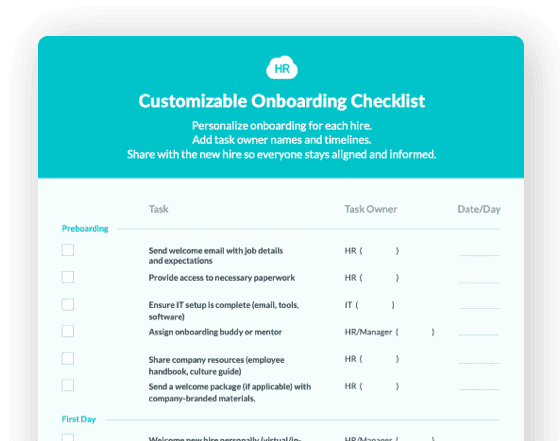
 Cut onboarding time
by 60%—here's the
Ultimate Checklist
that helped do it.
Cut onboarding time
by 60%—here's the
Ultimate Checklist
that helped do it.
Ask any administrative professional which department they think should manage cybersecurity for their organization, and they'll almost certainly say IT. Since the world moved to virtual offices en masse, it's become clear that HR department staffers have a huge role to play, even if it needs to be consistently recognized. Human resource workers who understand their company's vulnerabilities can put a stop to many attacks before they even get a chance to get going.
Some of the most sensitive data in the world passes through HR departments daily. Only accountants have regular access to riskier files. Training HR personnel to take a few extra precautions should be the first line of defense to protect this information.
Stopping Bad Actors In Their Tracks
An average data breach can cost around $4 million. Teaching HR department workers good password hygiene and firewall usage costs almost nothing. Security crackers actively listen to HR department communications to get login credentials to attack other parts of an organization. They also attempt to collect as much personal information as possible, which can be sold to support other criminal ventures financially.
Strong encryption algorithms would solve both of these problems. Everyone in the HR department needs to use end-to-end encryption systems whenever communicating with people outside of the organization. Those who have to send documents to outside groups should do so with a platform that offers at least a modicum of security.
Many HR heads will chime in by saying they already have plenty of security tools in place. However, recent changes have rendered some of the most popular encryption packages obsolete. HR workers should review what they're working with and see if they comply with the latest quantum-focused standards. Those using dated public-key algorithms will want to update them immediately.
HR workers can help foster a secure culture simply by keeping up with these changes and leading by example. In a worst-case scenario, HR specialists can implement disciplinary action to bring employees around. Reporting potentially illegal or unethical behavior for further investigation can help management and other departments pinpoint trouble areas.
Providing Important Security Insights
One of the biggest reasons employees start skirting internal security policies is that they need to be simplified. People will try to disable a firewall or malware scanner as soon as they feel inconvenienced by it. Information technology specialists might only realize people made a change once it's too late. Since HR managers oversee other employees, this behavior is usually apparent to them.
Setting good guidelines becomes much easier when technicians know how people respond to the old ones, so getting as much information as possible from the HR department is essential. These insights are also helpful when it comes time to write a contingency plan. Small—to medium-sized businesses must carry a cyber insurance policy that protects them against online risks. HR representatives know how much insurance an organization needs and how likely the company is to fall victim to certain attacks. This makes planning for future maladies much easier.
When it comes time to invest in new security software, they'll be the first to know which application failed in the past. Companies that deploy relatively quiet programs that don't interfere with daily workflows generally see the fewest complaints, which is why consulting with the HR department is vital. Supervisors will want to check their account records against HR department lists. If someone no longer works for a company, their account shouldn't work anymore. Gaining control of old logins is one of the easiest ways bad actors can find their way into a remote system.
Deciding Who Can Access Which Resources
File permissions are supposed to prevent unauthorized access to sensitive computer resources. However, they're often set wrong, so users can simply snoop on whatever documents they want.
IT staffers need to learn exactly what files people need daily. They're usually concerned with keeping everything up and running, so it falls on the HR department to make a map of each employee's requirements. Since HR workers must vet candidates when hiring new workers, they're uniquely qualified to find major red flags.
Nobody should have more digital authority than they need to do their job. If a person can accomplish their goals without being able to write to a specific database, then they should get ready only access. A roster of employees that spells out everyone's role is just the thing to help programmers create an accurate set of access controls.
According to one report, more than half of all breaches will result from human error in the coming years. Social engineering is among the most popular ways for bad actors to gain what superficially appears to be legitimate access to a system. HR experts would immediately know if someone was trying to impersonate someone else. Companies can rely on their HR departments to screen out suspected attempts and educate others on how to spot the telltale signs of a phishing attack.
Digital Segmentation Strategies That Actually Work
Even the most astute HR crew will end up with major headaches if people end up assigned to the wrong digital resource pool. Companies that have dedicated themselves to making sure that their individual staffers can only access certain cloud storage locations might end up hobbling their employees. Too much security is even worse than not enough since users who can't easily do their jobs are going to end up getting around whatever limitations are in place.
Computer experts can usually predict what cloud storage locations contain the greatest amount of sensitive data. It's often harder to predict which objects they'll need to look at in the future to answer customer questions or complete a project. That's another reason why it's so important to invite HR department representatives to every cybersecurity meeting.
Business managers usually use the word segmentation to refer to certain marketing practices, but it's also a good way to describe one of the most important cybersecurity planning steps. Organizations can start the process by making a list of all the objects they currently have stored in the cloud. Billing and payroll data will generally get closed out to all but a few select departments. Other databases, like those that contain customer lists and contact information, might present more of a challenge to planners.
Users who need to periodically access these documents will find ways to get into them if they're not given access. IT professionals can avoid this by initially giving read-only access to them based on suggestions provided by the HR team. Some adjustments will have to be made during the first few weeks that the new security system is in place. Things should run much more smoothly after a short trial period.
Moving Staffers Into A More Secure Cloud
Virtual onboarding paperwork can further simplify this procedure. New employees will get assigned to a digital resource pool based on their assumed responsibilities and the answers to their application form, thus saving a significant amount of time later on. This also means they can get to work as soon as they start without having to go through any awkward adjustment period.
Forward-thinking HR departments often poll the staffers in their organizations to see what changes have to be made during the next cycle. There's no reason why the results shouldn't also get forwarded over to those working in IT. Even the smallest tweak can help stop breaches before they happen.
Good password hygiene is vital, but it's often difficult to get employees to adhere to. Configuring the HR department's onboarding app to require new employees to create secure credentials from the beginning will help enforce these policies without any of the fuss.
Streamlining the sign-up process can make things so easy that new hires won't even realize they're working through a process many people find annoying.
Coordinating The HR and IT Departments
Creating an effective security policy will take more than one department, so coordinating efforts is essential. Though only some people get excited about meetings, it's a good idea to invite members of both departments to go over policy drafts and provide input.
Companies need to have measures in place that spell out the rules regarding data storage and authorized access. Regular check-in sessions are an excellent way to align technical and administrative goals. Anyone from either side who has a specific concern should feel free to share it.
Bringing legal experts onboard is also a good idea since there are countless regulatory constraints to deal with in this area. Each section of the company has a role to play. By incorporating everyone in the discussion, managers can craft inclusive policies that make sense for their organizations.
HR Cloud
Empower your HR team to champion cybersecurity. Provide tools to educate, engage, and safeguard your workforce against modern threats.
Author:
This article is written by Philip Piletic. His primary focus is a fusion of technology, small business, and marketing. He's a writer, marketing consultant, and guest author at several authority websites.
Keep Reading
The Ultimate Healthcare Onboarding Checklist: A Complete Guide for Healthcare Organizations
When Sarah, a newly hired ICU nurse at Denver Memorial Hospital, walked into her first
The Complete Guide to Employee Rewards Software with Gift Cards: Strategic Recognition in 2025
Employee gift card programs are transforming how organizations approach workplace
Top HR Platforms for Government Agencies: Complete 2025 Guide
Government agencies face unique HR challenges requiring specialized platforms that handle
Like What You Hear?
We'd love to chat with you more about how HR Cloud® can support your business's HR needs. Book Your Free Demo

Build a Culture of Recognition. Boost Engagement. Guaranteed.
Workmates empowers employees to stay informed, connected, and appreciated—whether they’re on the front line, in the office, or remote. Recognition drives 12x higher engagement.Trusted by industry leaders in every sector




Cut Onboarding Costs by 60%.
Take the confusion and follow-ups out of onboarding with automated workflows, digital forms, and structured portals—so new hires ramp faster 3X quicker.Trusted by industry leaders in every sector